NIS2 Directive – Obligations and Procedural Guidelines for Qualified Entities
In a previous blog article, we explained how to determine if your company qualifies under the NIS2 Directive. If you found that you meet the criteria, it’s time to understand what this entails in practice. The NIS2 Directive imposes specific obligations on companies to enhance their resilience to cyber threats and ensure digital security across Europe. In this article, we will outline the steps required to meet the new requirements, how to respond in case of an incident, and what penalties may arise for non-compliance. You’ll learn how to prepare your business for these new regulations to ensure the continuity and security of your operations.
Who Assesses the Company?
It is the responsibility of the business itself to independently analyze whether its size and the services it provides make it subject to the NIS2 Directive. This mechanism, known as self-identification, requires businesses to assess if they qualify as either “important” or “essential” entities. If this applies, they must register in the national registry for essential and important entities maintained by the appropriate national authorities. Essential and important entities must submit an electronic application for registration to the registry maintained by the Ministry of Digital Affairs within the timeframe specified by the ministry.
Obligations of Companies Subject to NIS2:
EU lawmakers have not specified the exact measures for each group of entities, but they have allowed a degree of flexibility. This means that companies must implement appropriate and proportionate cybersecurity risk management measures considering:
- the level of risk;
- the size of the entity;
- the likelihood and severity of incidents, including social and economic impacts.
To meet the requirement for cybersecurity risk management measures, the NIS2 Directive requires entities to ensure at least the following:
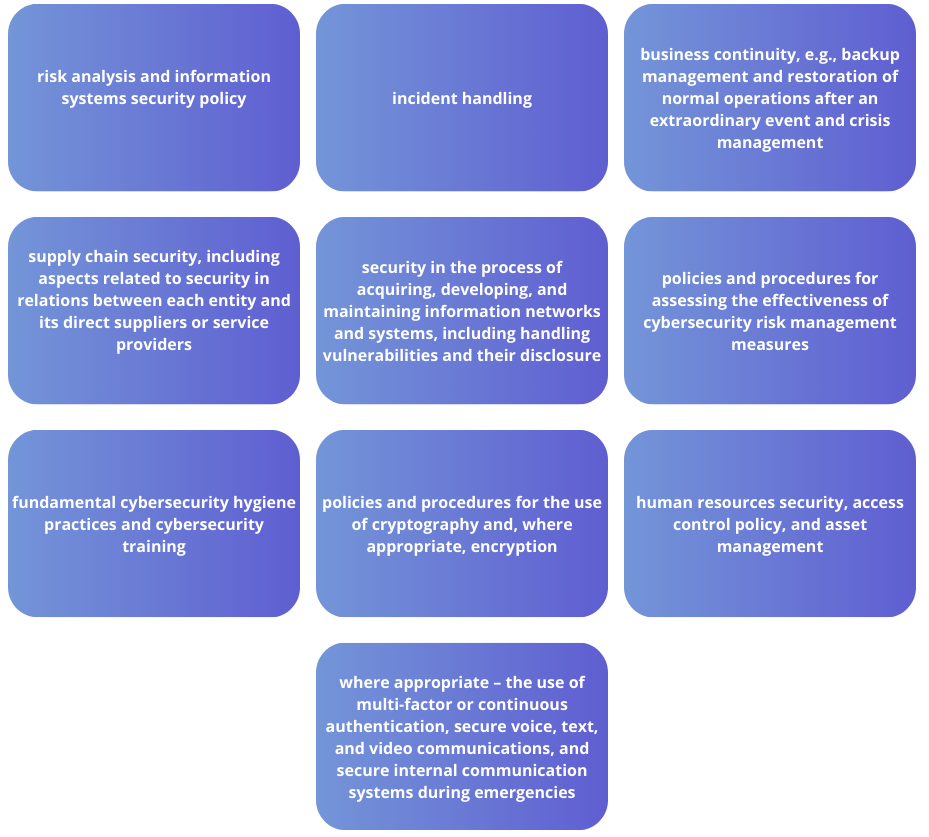
Entities are obligated to designate individuals or managing bodies within the company who approve cybersecurity risk management measures, oversee their implementation, and bear responsibility for potential breaches of the NIS2 Directive.
These individuals or bodies must undergo regular training to gain sufficient knowledge for correctly identifying and assessing cybersecurity risk management practices and their impact on the company’s services. While not mandatory, managers should also offer similar training to employees.
Incident Reporting
Companies are required to:
- Report significant incidents that impact the provision of services (serious incidents) to the relevant Computer Security Incident Response Team (CSIRT) or another designated authority (as defined by the law implementing the NIS2 Directive) without undue delay;
- Provide information that will help assess the cross-border impact of the incident;
- Notify service users of serious incidents that could negatively affect their access to services;
- Inform users potentially affected by a serious cyber threat about possible remedial measures and other steps they can take in response to the threat; where appropriate, they should also be informed about the nature of the cyber threat itself.
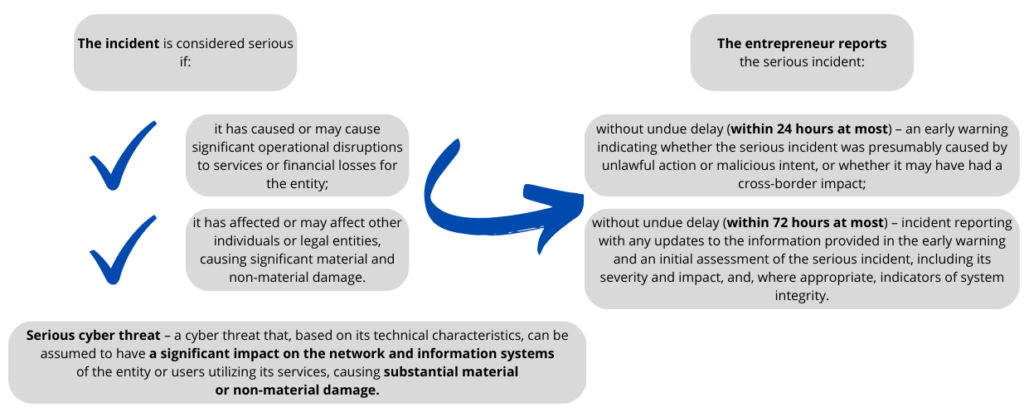
Trusted service providers must report serious incidents to the CSIRT or, as applicable, to the designated authority without undue delay, but no later than 24 hours after obtaining information about the incident.
Upon request by the CSIRT or relevant authority, an entity must submit:
- periodic reports on the status of the reported incident;
- a final report, no later than one month after the initial report (submitted within 72 hours of the incident).
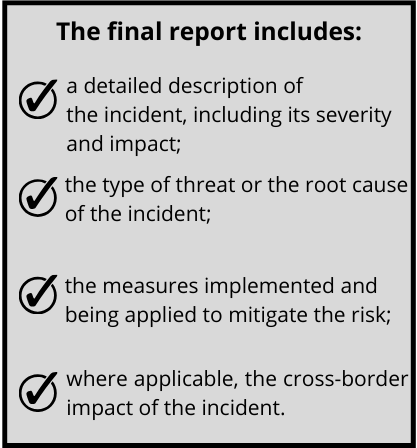
If the incident has not been resolved by the final report deadline, entities must submit a progress report at that time, with the final report due within a month after the incident is resolved.
If a serious incident affects at least two EU member states, the CSIRT, relevant authority, or single point of contact must inform the affected member states and ENISA (the European Union Agency for Cybersecurity) without undue delay.
Upon receiving an early warning, the CSIRT or designated authority must respond to the reporting entity by:
- providing initial feedback on the serious incident;
- offering operational guidance or advice on possible risk mitigation measures (at the entity’s request);
- providing additional technical support (upon request by the entity).
If the incident has criminal characteristics, the CSIRT or designated authority must also inform law enforcement.
If requested by the CSIRT or the relevant authority, the single point of contact must forward reports of cross-border or cross-sectoral incidents to single points of contact in other member states affected by the incident.
Certain categories of entities (including DNS service providers, TLD registry operators, and cloud service providers) will be covered by implementing acts that will specify serious incidents within their respective fields.
If the measures implemented by an entity are found to be non-compliant with the directive’s requirements, the entity must promptly implement corrective actions.
Penalties for Non-Compliance with NIS2 Directive Guidelines
The NIS2 Directive explicitly outlines financial consequences for failing to comply with its guidelines. For essential entities, failing to implement appropriate risk management measures or not reporting an incident could result in an administrative fine of up to €10 million or 2% of the company’s annual turnover, whichever amount is higher.
For important entities, slightly more lenient, but still significant, penalties apply—fines may reach up to €7 million or 1.4% of annual turnover, whichever is higher.
In addition, in cases of severe breaches, the directive provides for periodic financial penalties to encourage organizations to implement compliant measures.
Voluntary Disclosure of Critical Information
Voluntary disclosures to CSIRT or relevant authorities can be submitted by:
- essential and important entities in cases of incidents, cyber threats, or potential cybersecurity events;
- other entities, regardless of NIS2 coverage, concerning serious incidents, cyber threats, and potential cybersecurity events.
Voluntary reports are handled similarly to mandatory serious incident reports, although mandatory reports may be prioritized.
If necessary, reports are shared with single points of contact while maintaining confidentiality and protecting the information provided by the reporting entity. Voluntary reports do not impose additional obligations on the reporting entity.
You can read the full NIS2 Directive here.
Compliance with the NIS2 Directive is essential, not only to meet new legal standards but also to genuinely increase the resilience of your company to cyber threats and secure its digital services and data. Implementing proper risk management measures and readiness for incident response may seem demanding, but they are crucial steps in protecting business operations and customer trust.
If you have any questions about NIS2 requirements or need support in developing security procedures, feel free to contact us at Konwerga. Our specialists will help you implement solutions tailored to your needs, enabling you to meet the obligations of the new regulations and protect your business from cyber threats.
